This morning, I discovered that I could no longer connect to one of my Mikrotik routers via OpenVPN using Tunnelblick. The Mikrotik is still running 6.49, and OpenVPN configuration was originally created back in 2020.
The router is located 2000 km away from me, so I started to get a bit nervous. Fortunately, the same OpenVPN client profile worked fine on another machine and on my iPhone, which allowed me to access the console and confirm that the issue was not the Mikrotik itself.
Thats all I was able to discover in the Mikrotik logs
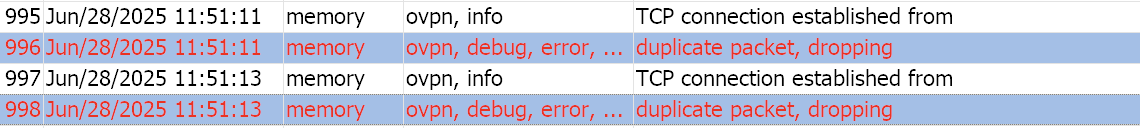
And the Tunnelblick logs were not giving much of an explanation either:
2025-06-28 12:51:11.469249 TCP/UDP: Preserving recently used remote address: [AF_INET]xx.xx.xx.xx:xxxx
2025-06-28 12:51:11.469384 Socket Buffers: R=[131072->131072] S=[131072->131072]
2025-06-28 12:51:11.469404 Attempting to establish TCP connection with [AF_INET]xx.xx.xx.xx:xxxx
2025-06-28 12:51:11.469419 MANAGEMENT: >STATE:1751100671,TCP_CONNECT,,,,,,
2025-06-28 12:51:11.505709 TCP connection established with [AF_INET]xx.xx.xx.xx:xxxx
2025-06-28 12:51:11.505793 TCPv4_CLIENT link local: (not bound)
2025-06-28 12:51:11.505814 TCPv4_CLIENT link remote: [AF_INET]xx.xx.xx.xx:xxxx
2025-06-28 12:51:11.505872 MANAGEMENT: >STATE:1751100671,WAIT,,,,,,
2025-06-28 12:51:11.542457 MANAGEMENT: >STATE:1751100671,AUTH,,,,,,
2025-06-28 12:51:11.542573 TLS: Initial packet from [AF_INET]xx.xx.xx.xx:xxxx, sid=00f38fff c2df36c9
2025-06-28 12:51:11.859129 VERIFY OK: depth=1, CN=homeline
2025-06-28 12:51:11.860552 VERIFY KU OK
2025-06-28 12:51:11.860608 Validating certificate extended key usage
2025-06-28 12:51:11.860621 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2025-06-28 12:51:11.860632 VERIFY EKU OK
2025-06-28 12:51:11.860643 VERIFY OK: depth=0, CN=server
2025-06-28 12:51:12.022322 Connection reset, restarting [0]
2025-06-28 12:51:12.022592 SIGUSR1[soft,connection-reset] received, process restarting
2025-06-28 12:51:12.022824 MANAGEMENT: >STATE:1751100672,RECONNECTING,connection-reset,,,,,
2025-06-28 12:51:12.024635 *Tunnelblick: Delaying HOLD release for 1.000 seconds
While searching online, I discovered that similar issues had been reported several years ago, which made me think the answer might lie in the OpenVPN release notes.
I remembered that I had to upgrade to a newer version of OpenVPN at some point because one of the servers refused to communicate with the older client.
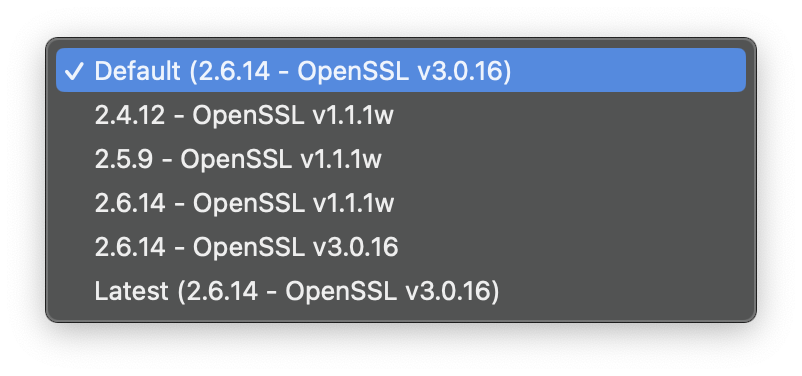
After quickly scanning the release logs, I found the following note:
2.4.x or lower: The cipher in --cipher is appended to --data-ciphers.
Apperently starting from version 2.5 --data-ciphers option defaults to an empty value? So fixing an issue was just a oneline change to my client.ovpn config file:
cipher AES-256-CBC
+data-ciphers AES-256-CBC
Maybe one day I will upgrade to RouterOS v7, considering that most of the functionality should work and it has WireGuard support.